Managing secrets in open source iOS apps
One of the issues that open source authors have to deal with is secrets management. The small utility app I’m working on relies on Dropbox API. Before you can work with Dropbox API though, you have to generate an API key. The API key identifies the application to Dropbox and needs to remain mostly secret. A bad actor could impersonate the application author by stealing the API key.
This is a long winded way of saying that API keys must be kept out of public repositories. How can this be achieved?
Turns out it’s fairly straightforward. Xcode supports configuration schemes, via xcconfig files.
The process is straightforward.
- Create a new configuration settings file (via File > New File, use the filter box)
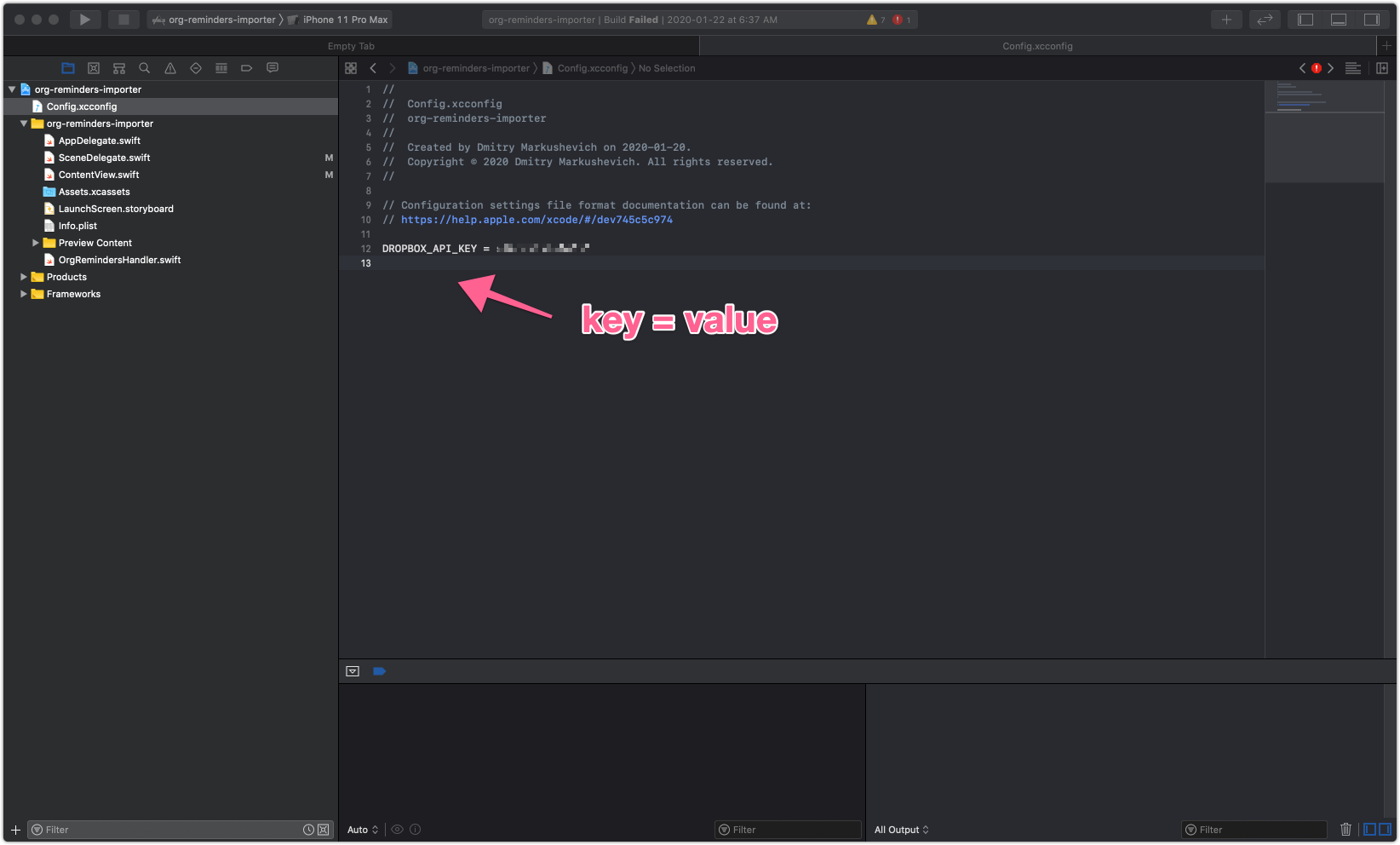
- Add the settings to file the (the format is
key = value) - Specify the configuration in project target
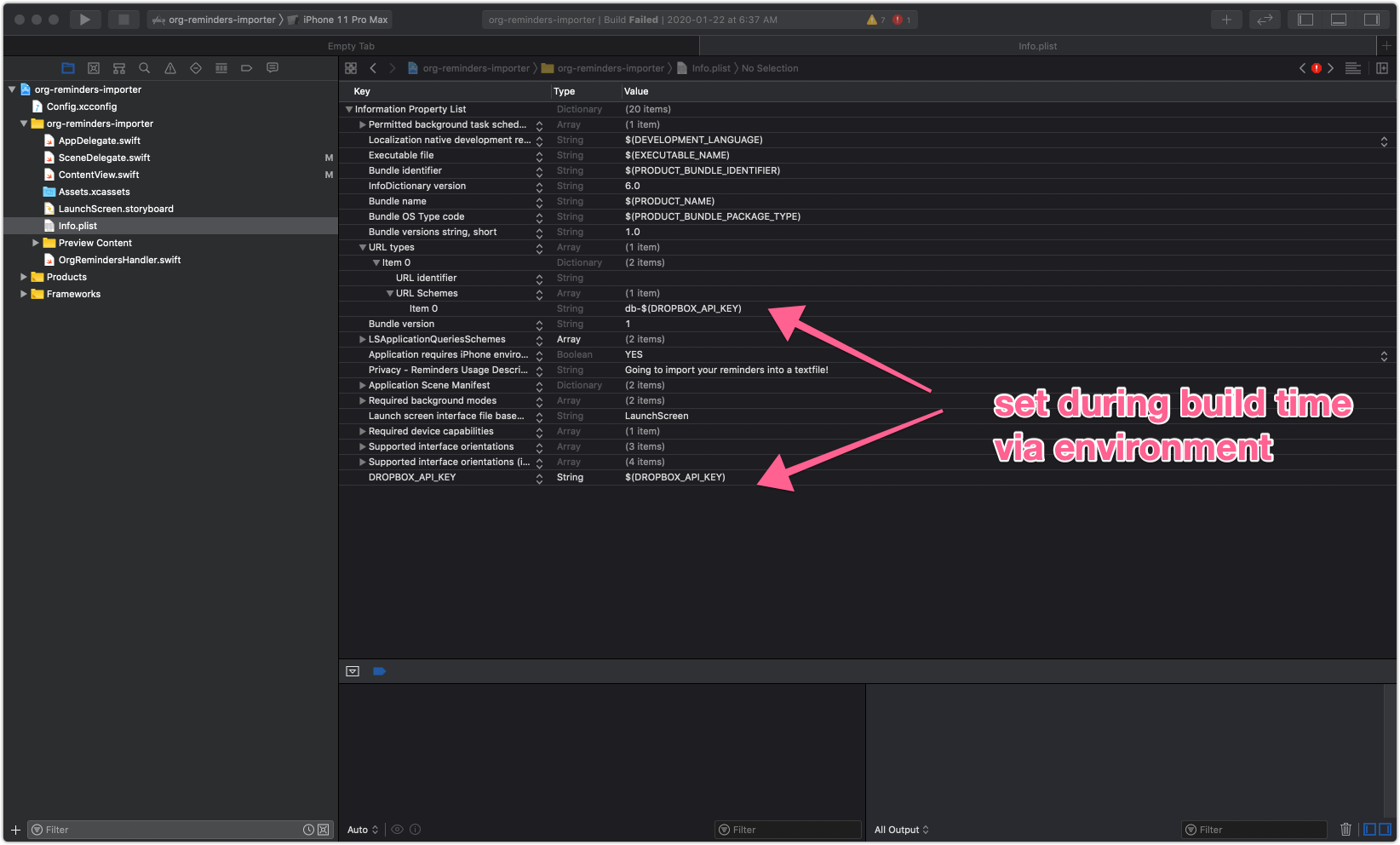
- Configure the
Info.plistfile (see below) - Use in code.
Config file and settings
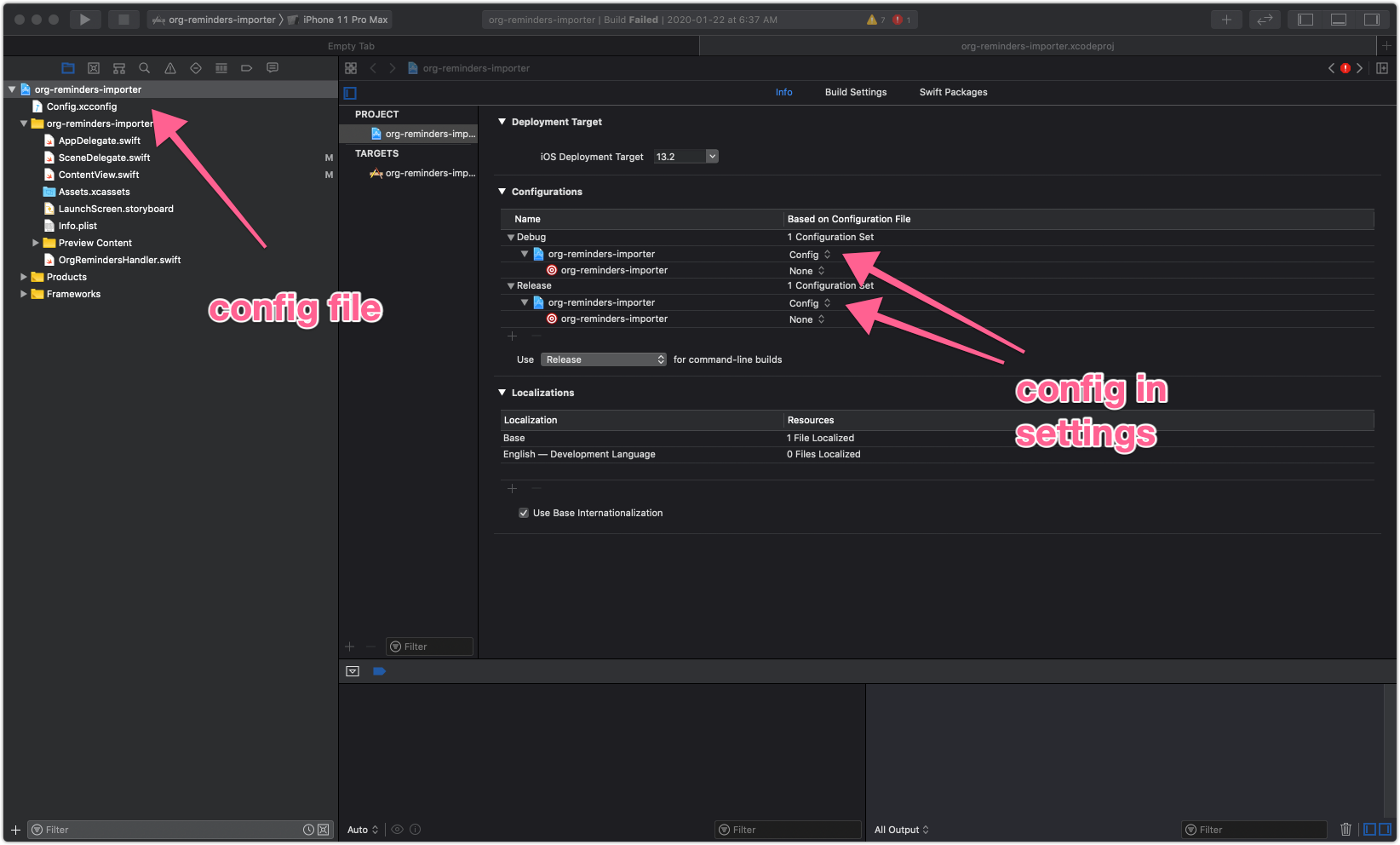
Contents of the config file
Info.plist
qq**** Using the variables in code
Info.plist values are going to be set at compile time. To retrieve them something like this can be used:
let dropBoxApiKey = Bundle.main.object(forInfoDictionaryKey:"DROPBOX_API_KEY")
References
There’s some additional info in the following posts:
- Managing secrets within an iOS app | Lord Codes
- Keeping secrets out of Git in iOS
- Using Xcode Configuration (.xcconfig) to Manage Different Build Settings
PS: Removing sensitive data from git history
I would be remiss if I didn’t include instructions on how to remove sensitive data from you repository’s history.